An HTTP cookie is data stored on a user's computer that assists in automated access to websites or web features, or other state information required in complex web sites. It may also be used for user-tracking by storing special usage history data in a cookie, and such cookies — for example, those used by Google Analytics — are called tracking cookies. Mar 21, 2021 To protect your online privacy, ignore the 'About Me' fields in your social media profiles. You don't have to let people know what year or where you were born — which could make you an easier target for identity theft. Explore different privacy settings, too. You might want to limit the people who can view your posts to those you've.
- Cookie 4 5 4 – Protect Your Online Privacy Policy
- Cookie 4 5 4 – Protect Your Online Privacy Rule
- Cookie 4 5 4 – Protect Your Online Privacy Statement
April 2002
by Stanton McCandlish, EFF Technology Director
Vers. 2.0 - Apr. 10, 2002
Note: Mention of specific product, service or company names does
not constitute EFF endorsement or recommendation. Examples and links
are provided as starting points for readers, who must make up their
own minds about how much security they need and whether particular
offerings will suit their needs.
For information about the law and technology of government surveillance in the United States, check out EFF's Surveillance Self-Defense project.
1) Do not reveal personal information inadvertently.
You may be 'shedding' personal details, including e-mail addresses
and other contact information, without even knowing it unless you
properly configure your Web browser. In your browser's 'Setup',
'Options' or 'Preferences' menus, you may wish to use a pseudonym instead of your real name, and
not enter an e-mail address, nor provide other personally identifiable
information that you don't wish to share. When visiting a site you
trust you can choose to give them your info, in forms on their site;
there is no need for your browser to potentially make this information
available to all comers. Also be on the lookout for system-wide
'Internet defaults' programs on your computer (some examples include
Window's Internet Control Panel, and MacOS's Configuration Manager,
and the third-party Mac utility named Internet Config). While they are useful
for various things, like keeping multiple Web browers and other
Internet tools consistent in how the treat downloaded files and such,
they should probably also be anonymized just like your browser itself,
if they contain any fields for personal information. Households with
children may have an additional 'security problem' - have you set
clear rules for your kids, so that they know not to reveal personal
information unless you OK it on a site-by-site basis?
2) Turn on cookie notices in your Web browser, and/or use cookie management software or infomediaries.
'Cookies' are tidbits of information that Web sites store on your
computer, temporarily or more-or-less permanently. In many cases
cookies are useful and inocuous. They may be passwords and user IDs,
so that you do not have to keep retyping them every time you load a
new page at the site that issued the cookie. Other cookies however, can be used for 'data
mining' purposes, to track your motions through a Web site, the time
you spend there, what links you click on and other details that the
company wants to record, usually for marketing purposes. Most cookies
can only be read by the party that created them. However, some companies
that manage online banner advertising are, in essence, cookie sharing rings. They
can track which pages you load, which ads you click on, etc., and share this information
with all of their client Web sites (who may number in the hundreds, even thousands.) Some
examples of these cookie sharing rings are DoubleClick, AdCast
and LinkExchange. For a demonstration of how they work, see:
http://privacy.net/track/
Browsers are starting
to allow user control over cookies. Netscape, for example, allows you
to see a notice when a site tries to write a cookie file to your hard
drive, and gives you some information about it, allowing you to decide
whether or not to accept it. (Be on the lookout for cookies the
function of which is not apparent, which go to other sites than the one you are trying to load, or which
are not temporary). It also allows you to automatically block all
cookies that are being sent to third parties (or to block all cookies,
entirely, but this will make some sites inoperable). Internet
Explorer has a cookie management interface in addition to
Netscape-like features, allowing you to selectively enable or disable
cookies on a site-by-site basis, even to allow cookies for a site
generally, but delete a specific cookie you are suspicious about. With
Internet Explorer you can also turn on cookies for a site temporarily
then disable them when you no longer need them (e.g., at an online
bookstore that requires cookies to process an order, but whom you
don't want to track what books you are looking at, what links you are
following, etc., the rest of the time.) Turning on cookie warnings
will cause alert boxes to pop up, but after some practice you may learn
to hit 'Decline' so fast that you hardly notice them any more. The
idea is to only enable cookies on sites that require them AND whom you
trust.
You may also wish to try out 'alternative' browsers like
Mozilla (Windows, Mac, Linux), Opera (Windows, Mac, Linux), Konqueror (Linux),
and iCab (Mac), which may offer better cookie management.
You can also use cookie management software and services. One example is
the Internet Junkbuster Proxy ( http://www.junkbusters.com/ht/en/ijb.html ).
It runs on Win95/98/NT and
Unix/Linux
(no Mac version), and can selectively
block cookies for you (and banner ads, to boot). interMute ( http://www.intermute.com/ )
does likewise (and more - blocks popup windows, etc.; only runs under Windows).
Another Windows-only
solution is AdSubtract ( http://www.adsubtract.com/ )
A comparable product (Linux, Solaris, Windows) is GuideScope ( http://www.guidescope.com/home/ )
A Java-based solution called Muffin ( http://muffin.doit.org/ ) is also available. While it will run
on Mac, Windows and Unix systems, it is definitely for 'power users', as it is complicated
to set up and operate effectively.
Another recent option (Linux, Mac, Windows) is the
( http://www.webwasher.com/ ), which has advanced cookie filtering capabilities,
especially with the Seclude-It and Secretmaker plug-ins available at the same site.
One more (Windows) is CookiePal ( http://www.kburra.com/cpal.html ),
and yet another (Windows) is ( http://www.thelimitsoft.com/cookie.html ).
There are also numerous 'cookie eater' applications,
some which run on a schedule or in the background, that delete cookie files for you. As with turning off
cookies entirely, you may have trouble accessing sites that require certain cookies (though
in most cases the worst that will happen is that you'll have to re-enter a login ID and password
you thought were saved.) 'Eating' the cookies periodically still permits sites to track what
you're doing for a short time (i.e., the time between successive deletion of your cookie file),
but thwarts attempts to discern and record your actions over time.
Yet another option is to use an 'infomediary' (some are home-use software products, others may be network-based services),
such as SeigeSoft's
SiegeSurfer ( http://www.siegesoft.com/_html/tutorial.asp ),
Zero Knowledge Systems' Freedom
( http://www.freedom.net ), among others. These products/services act as a proxy or
shield between you and sites you visit, and can completely disguise to Web sites where you are coming from
and who you are (and intercept all cookies). Most are Windows-only at this point, though
Orangatango ( http://www.orangatango.com/ ), and SafeWeb
and ( http://www.safeweb.com ) also offer
such services that are Web-based and not platform-dependent.
WARNING: Do not confuse honest infomediaries
with 'identity managmenet services' like Microsoft's Passport service or Novell's DigitalMe. While you may gain some
temporary convenience at sites that support them, you'll lose essential privacy, because these services are not
there to serve you but to serve marketing purposes by collecting a vast array of information about you and selling it.
The best solution doesn't exist yet: Full cookie management abilities built
into the browsers themselves. Only increased user pressure on Microsoft, Netscape
and other browser makers can make this happen. Users should ultimately be able
to reject cookies on a whole-domain basis, reject all third-party cookies by default, reject all cookies that are not essential
for the transaction at hand, receive notice of exactly what a cookie is intended for,
and be able to set default behaviors and permissions rather than have to interact with cookies on a page-by-page
basis. This just isn't possible yet. You may wish to contact the company that makes your browser software and
demand these essential features in the next version.
3) Keep a 'clean' e-mail address.
When mailing to unknown parties; posting to newsgroups, mailing
lists, chat rooms and other public spaces on the Net; or publishing a
Web page that mentions your e-mail address, it is best to do this from
a 'side' account, some pseudonymous or simply alternate address, and
to use your main or preferred address only on small, members-only
lists and with known, trusted individuals. Addresses that are posted
(even as part of message headers) in public spaces can be easily
discovered by spammers (online junk mailers) and added to their list of
targets. If your public 'throw away' address gets spammed enough to become
annoying, you can simply kill it off, and start a new one. Your
friends, boss, etc., will still know your 'real' address. You can use
a free (advertising-supported) e-mail service provider like Yahoo Mail
or Hotmail for such 'side' accounts. It is best to use a 'real'
Internet service provider for your main account, and to examine their
privacy policies and terms of service, as some 'freemail' services may have
poor privacy track records. You may find it works best to use an
e-mail package that allows mulitiple user IDs and addresses (a.k.a.
'personalities', 'aliases') so that you do not have to switch between multiple
programs to manange and use more than one e-mail address
(though you may
have to use a Web browser rather than an e-mail program to read your
mail in your 'throw away' accounts - many freemail providers do not
allow POP or IMAP connections). If you are 'required'
to give an e-mail address to use a site (but will not be required to
check your mail for some kind of access code they send you), you can
use 'someuser@example.com' (example.com is a non-existent site,
set up by the Internet standards to be used as an example that will
never accidentally coincide with anyone's real e-mail address, which
is always a danger if you just make up one off the top of your head.)
4) Don't reveal personal details to strangers or just-met
'friends'.
The speed of Internet communication is often
mirrored
in rapid online
acquaintanceships and friendships. But it is important to realize that
you don't really know who these people are or what they are like in
real life. A thousand miles away, you don't have friends-of-friends
or other references about this person. Be also wary of face-to-face
meetings. If you and your new e-friend wish to meet in person, do it
in a public place. Bringing a friend along can also be a good idea.
One needn't be paranoid, but one should not be an easy mark, either.
Some personal information you might wish to withhold until you know
someone much better would include your full name, place of employment,
phone number, and street address (among more obvious things like
credit card numbers, etc.) Needless to say, such information should
not be put on personal home pages. (If you have a work home page, it
may well have work contact information on it, but you needn't reveal
this page to everyone you meet in a chat room.) For this and other
reasons, many people maintain two personal home pages, a work-related
one, and an 'off duty' version. In the commercial sector, too, beware
'fast-met friends'. A common
'social engineering'
form
of industrial espionage is to befriend someone online just long
enough to get them to reveal insider information.
5) Realize you may be monitored at work, avoid sending highly
personal e-mail to mailing lists, and keep sensitive files on your
home computer.
In most US states and many if not most countries, employees have little if any privacy protection
from monitoring by employers. When discussing sensitive matters in
e-mail or other online media, be certain
with whom you are communicating
. If
you replied to a mailing list post, check the headers - is your reply
going to the person you think it is, or to the whole list? Also be
aware that an increasing number of employers are monitoring and
recording employee Web usage, as well as e-mail. This could compromise
home banking passwords and other sensitive information. Keep private
data and private Net usage

private
, at home.
See this CNN/IDG article on 'snoopware' (which may not be limited to your office..):
6) Beware sites that offer some sort of reward or prize in
exchange for your
contact information or other personal details
.
There's a very high probability that they are gathering this
information for direct marketing purposes. In many cases your name and
address are worth much more to them because they can sell it to other
marketers (who can do the same in turn..) than what
you are (supposedly) getting from them. Be especially wary of
sweepstakes and contests. You probably won't win, but the marketer
sure will if you give them your information.
7) Do not reply to spammers, for any reason.
'Spam', or unsolicited bulk e-mail, is something you are probably
already familiar with (and tired of). If you get a spammed
advertisment, certainly don't take the sender up on whatever offer
they are making, but also don't bother replying with 'REMOVE' in the
subject line, or whatever (probably bogus) unsubscribe instructions
you've been given). This simply confirms that your address is being
read by a real person, and you'll find yourself on dozens more
spammers' lists in no time. If you open the message, watch your
outgoing mail queue to make sure that a 'return receipt' message was
not generated to be sent back to the spammer automatically. (It is
best to queue your mail and send manually, rather than send
immediately, so that you can see what's about to go out before it's
actually sent. You should also turn off your mailer's automatic
honoring of return receipt requests, if any.) If you have a good
Internet service provider, you may
be able to forward copies of spam e-mail to the system administrators
who can route a complaint to the ISP of the spammer (or if you know a
lot about mail headers and DNS tools, you can probably contact these
ISPs yourself to complain about the spammer.) If you are getting
spammed a lot, there are a variety of filters and anti-spam
services available, including:
Spam Hater ( http://www.cix.co.uk/~net-services/spam/spam_hater.htm ) for Windows users;
TAG ( http://alcor.concordia.ca/topics/email/auto/procmail/spam ) for experienced Unix users;
SpamBouncer ( http://www.spambouncer.org ) for experienced Unix users (works well with TAG);
BrightMail ( http://www.brightmail.com/ ) for ISPs;
SpamCop ( http://spamcop.net/ ) for anyone;
More information on fighting spam is available at:
Elsop's Anti-Spam Page ( http://www.elsop.com/wrc/nospam.htm );
MaximumDownforce's Info-n-Links Page( http://www.maximumdownforce.com/hotlinks.html ); Wifi explorer 1 7 2 download free.
Whew's Anti-Spam Campaign ( http://www.whew.com/Spammers/ ).
Many of these are difficult to use for novices, and some require Unix
expertise. Others are services that deal with ISPs only, not end users.
8) Be conscious of Web security.
Never submit a credit card number or other highly sensitive
personal information without first making sure your connection is
secure (encrypted). In Netscape, look for an closed lock (Windows) or unbroken key (Mac) icon at the
bottom of the browser window. In Internet Explorer, look for a closed
lock icon at the bottom (Windows) or near the top (Mac) of the browser window.
In any browser, look at
the URL (Web address) line - a secure connection will begin 'https://'
intead of 'http://'. If you are at page that asks for such information
but shows 'http://' try adding the 's' yourself and hitting enter to
reload the page (for Netscape or IE; in another browser, use whatever method is required
by your browser to reload the page at the new URL). If you get an
error message that the page or site does not exist, this probably
means that the company is so clueless - and careless with your
information and your money - that they don't even have Web security.
Take your business elsewhere.
Your browser itself gives away information about you, if your IP address
can be tied to your identity (this is most commonly true of DSL and broadband
users, rather than modem users, who are a dwindling minority). For a demo
of how much detail is automatically given out about your system by your
browser, see: http://privacy.net/analyze/ .
Also be on the lookout for 'spyware' - software that may be included
with applications you install (games, utilities, whatever), the
purpose of which is to silently spy on your online habits and other
details and report it back to the company whose product you are using.
One MS Windows solution for disabling spyware is the Ad-aware program
(shareware, from http://www.lavasoft.de/ ),
which can remove spyware from your computer; it is based on a large
collaboratively maintained database of information about spyware.
Linux and Mac products of this sort are likely to appear soon.
Java, Javascript and ActiveX can also be used for spyware purposes.
Support for these scripting languages can be disabled in your
browser's configuration options (a.k.a. preferences, settings,
or properties). It is safest to surf with them turned off,
and only turn them on when a site you trust and want to use
requires them. If you don't know if your browser supports these
languages or don't know if they are turned on you can use BrowserSpy
to find out (along with a lot of other information about your Web
browsing software): http://gemal.dk/browserspy/
Another form of spyware consists of 'webbugs', which typically
manifest themselves as invisible or nearly invisible image files
tied to cookies and javascripts that track your Web usage.
See http://www.google.com/search?hl=en&q=webbugs+%22web+bugs%22
for more information on webbugs. See also this webbug FAQ, http://www.nthelp.com/OEtest/web_bug_faq.htm for more details.
Dealing with webbugs when they are embedded in an otherwise legitimate page
is thorny, as there isn't a surefire way to distinguish between webbugs and
run-of-the-mill image files. But see the Privacy Foundation's
Bugnosis webbug detector ( http://www.bugnosis.org/ - Windows MSIE only).
When webbugs are loaded into popup pages, the solution is to close the popups
(usually a small page with an ad, though some of them are 'micropages'
that you can barely see. A few may even use javascript tricks to keep
you from closing them. If this happens, close all other browser windows,
then you should be able to close the bug window). Another tip for defeating
webbugs is to reject any cookies from Doubleclick, AdCast, LinkExchange and other
'ad exchange networks' (cookie sharing rings), and any other cookies that
are not from the site you are currently visiting (most third-party cookies
are basically webbugs). Lastly on this topic, be aware that HTML-capable
e-mail programs and Usenet newsreaders make webbugs work in your e-mail
and newsgroups. If your mailer or newsreader has an option to turn off
cookie support, you should certainly do so. There is hardly any imaginable
legitimate use for a cookie in an email or a newsgroup posting.
9) Be conscious of home computer security.
On the other side of the coin, your own computer may be a trouble
spot for Internet security.
If you have a DSL line, broadband cable modem or other connection
to the Internet that is up and running 24 hours (including T1 at the office without a firewall
or NAT),
unlike a modem-and-phone-line connection, be sure to turn your computer off
when you are not using it. Most home PCs have pitifully poor security
compared to the Unix workstations that power most commercial Web
sites. System crackers search for vulnerable, unattended DSL-connected
home computers, and can invade them with surprising ease, rifiling
through files looking for credit card numbers or other sensitive data,
or even 'taking over' the computer and quietly using it for their own
purposes, such as lauching attacks on other computers elsewhere -
attacks you could initially be blamed for. Firewall hardware and software is
another option that can protect you from these kinds of attacks (available
at any computer store; freeware and shareware implementations may be
available at sites like http://www.shareware.com
or http://www.download.com.
10) Examine privacy policies and seals.
When you are considering whether or not to do business with a Web
site, there are other factors than a secure connection you have to consider that are equally
important to Web security. Does the site provide offline contact
information, including a postal address? Does the site have a
prominently-posted privacy policy? If so, what does it say? (Just
because they call it a 'privacy policy' doesn't mean it will protect
you - read it for yourself. Many are little more than disclaimers
saying that you have no privacy! So read them carefully.) If the
policy sounds OK to you, do you have a reason to believe it? Have you
ever heard of this company? What is their reputation? And are they
backing up their privacy statement with a seal program such as TRUSTe
http://www.truste.org/ or
BBBonline http://www.bbbonline.org/? (While imperfect, such
programs hold Web sites to at least some minimal baseline standards, and may revoke, with much fanfare, the
approval-seal licenses of bad-acting companies that do not
keep their word.) If you see a seal, is it real? Check with the
seal-issuing site to make sure the seal isn't a fake. And examine
terms carefully, especially if you are subscribing to a service rather
than buying a product. Look out for auto-rebilling scams and hidden
fees.
11) Remember that YOU decide what information about yourself to
reveal, when, why, and to whom.
Don't give out personally-identifiable information too easily. Just as
you might think twice about giving some clerk at the mall your home
address and phone number, keep in mind that simply because a site asks
for or demands personal information from you does not mean you have to
give it. You do have to give accurate billing information if you are
buying something, of course, but if you are registering with a free
site that is a little too nosy for you, there is no law (in most places) against
providing them with pseudonymous information. (However, it would
probably be polite to use obviously fake addresses, such as '123 No
Such Street, Nowhere, DC 01010'. If they are generating mailings based
on this information - presumably in accordance with the terms of their
privacy policy - they can probably weed such addresses out and not
waste the postage on them. Definitely do NOT use someone else's real
address!)
However, if you are required to agree to
terms of service before using the free service, be sure those terms
do not include a requirement that you provide correct information,
unless the penalty is simply not being allowed to use the service
any more, and you're willing to pay that price if they figure out
you are not providing them with your actual personally-identifiable
information.
12) Use encryption!
Last but certainly not least, there are other privacy threats
besides abusive marketers, nosy bosses, spammers and scammers. Some
of the threats include industrial espionage, government surveillance,
identity theft, disgruntled former associates, and system crackers.
Relatively easy-to-use e-mail and file encryption software is
available for free, such as Pretty Good Privacy (PGP, available at: http://www.pgpi.org/), which runs on
almost all computers and even integrates seamlessly with most major
e-mail software. Good encryption uses very robust secret codes, that
are difficult if not impossible to crack, to protect your data. You
can also use specialized services (some free, some pay)
that go beyond infomediary services, including running all connections
through a securely encrypted 'tunnel', anonymous dialup, even anonymous
Web publishing. Another type of product is SSH tunnelling (port forwarding) packages, such as FSecure SSH ( http://www.fsecure.com/products/ssh/ ),
and SecureCRT ( http://www.vandyke.com/products/securecrt/ ).
Hopefully some day soon, good encryption and computer security will simply
be included in all ISP services and operating systems, but for now you have to actively
seek out good service providers and add-on products.
For more information on protecting your online privacy:
- EFF Privacy Archive - http://www.eff.org/Privacy/
- 'Protecting Yourself Online' Book -
- TRUSTe's 'Protecting Your Privacy Online' FAQ - http://truste.org/consumers/users_faqs.html
- Privacy Rights Clearinghouse - http://www.privacyrights.org/
- Privacy International - http://www.privacyinternational.org/
Over the last few decades, the world has changed tremendously in many regards, especially when it comes to IT. The number of people we are able to communicate with on a daily basis has grown enormously, just like the amount of information we have access to. However, the same is true for the amount of information big companies collect about us. Terms such as big data are used all the more frequently as time goes on. But what does this mean, exactly? What is big data? Is it dangerous? How does it affect our privacy, if at all? Those are some of the questions we'll cover in this article.
private
, at home.
See this CNN/IDG article on 'snoopware' (which may not be limited to your office..):
6) Beware sites that offer some sort of reward or prize in
exchange for your
contact information or other personal details
.
There's a very high probability that they are gathering this
information for direct marketing purposes. In many cases your name and
address are worth much more to them because they can sell it to other
marketers (who can do the same in turn..) than what
you are (supposedly) getting from them. Be especially wary of
sweepstakes and contests. You probably won't win, but the marketer
sure will if you give them your information.
7) Do not reply to spammers, for any reason.
'Spam', or unsolicited bulk e-mail, is something you are probably
already familiar with (and tired of). If you get a spammed
advertisment, certainly don't take the sender up on whatever offer
they are making, but also don't bother replying with 'REMOVE' in the
subject line, or whatever (probably bogus) unsubscribe instructions
you've been given). This simply confirms that your address is being
read by a real person, and you'll find yourself on dozens more
spammers' lists in no time. If you open the message, watch your
outgoing mail queue to make sure that a 'return receipt' message was
not generated to be sent back to the spammer automatically. (It is
best to queue your mail and send manually, rather than send
immediately, so that you can see what's about to go out before it's
actually sent. You should also turn off your mailer's automatic
honoring of return receipt requests, if any.) If you have a good
Internet service provider, you may
be able to forward copies of spam e-mail to the system administrators
who can route a complaint to the ISP of the spammer (or if you know a
lot about mail headers and DNS tools, you can probably contact these
ISPs yourself to complain about the spammer.) If you are getting
spammed a lot, there are a variety of filters and anti-spam
services available, including:
Spam Hater ( http://www.cix.co.uk/~net-services/spam/spam_hater.htm ) for Windows users;
TAG ( http://alcor.concordia.ca/topics/email/auto/procmail/spam ) for experienced Unix users;
SpamBouncer ( http://www.spambouncer.org ) for experienced Unix users (works well with TAG);
BrightMail ( http://www.brightmail.com/ ) for ISPs;
SpamCop ( http://spamcop.net/ ) for anyone;
More information on fighting spam is available at:
Elsop's Anti-Spam Page ( http://www.elsop.com/wrc/nospam.htm );
MaximumDownforce's Info-n-Links Page( http://www.maximumdownforce.com/hotlinks.html ); Wifi explorer 1 7 2 download free.
Whew's Anti-Spam Campaign ( http://www.whew.com/Spammers/ ).
Many of these are difficult to use for novices, and some require Unix
expertise. Others are services that deal with ISPs only, not end users.
8) Be conscious of Web security.
Never submit a credit card number or other highly sensitive
personal information without first making sure your connection is
secure (encrypted). In Netscape, look for an closed lock (Windows) or unbroken key (Mac) icon at the
bottom of the browser window. In Internet Explorer, look for a closed
lock icon at the bottom (Windows) or near the top (Mac) of the browser window.
In any browser, look at
the URL (Web address) line - a secure connection will begin 'https://'
intead of 'http://'. If you are at page that asks for such information
but shows 'http://' try adding the 's' yourself and hitting enter to
reload the page (for Netscape or IE; in another browser, use whatever method is required
by your browser to reload the page at the new URL). If you get an
error message that the page or site does not exist, this probably
means that the company is so clueless - and careless with your
information and your money - that they don't even have Web security.
Take your business elsewhere.
Your browser itself gives away information about you, if your IP address
can be tied to your identity (this is most commonly true of DSL and broadband
users, rather than modem users, who are a dwindling minority). For a demo
of how much detail is automatically given out about your system by your
browser, see: http://privacy.net/analyze/ .
Also be on the lookout for 'spyware' - software that may be included
with applications you install (games, utilities, whatever), the
purpose of which is to silently spy on your online habits and other
details and report it back to the company whose product you are using.
One MS Windows solution for disabling spyware is the Ad-aware program
(shareware, from http://www.lavasoft.de/ ),
which can remove spyware from your computer; it is based on a large
collaboratively maintained database of information about spyware.
Linux and Mac products of this sort are likely to appear soon.
Java, Javascript and ActiveX can also be used for spyware purposes.
Support for these scripting languages can be disabled in your
browser's configuration options (a.k.a. preferences, settings,
or properties). It is safest to surf with them turned off,
and only turn them on when a site you trust and want to use
requires them. If you don't know if your browser supports these
languages or don't know if they are turned on you can use BrowserSpy
to find out (along with a lot of other information about your Web
browsing software): http://gemal.dk/browserspy/
Another form of spyware consists of 'webbugs', which typically
manifest themselves as invisible or nearly invisible image files
tied to cookies and javascripts that track your Web usage.
See http://www.google.com/search?hl=en&q=webbugs+%22web+bugs%22
for more information on webbugs. See also this webbug FAQ, http://www.nthelp.com/OEtest/web_bug_faq.htm for more details.
Dealing with webbugs when they are embedded in an otherwise legitimate page
is thorny, as there isn't a surefire way to distinguish between webbugs and
run-of-the-mill image files. But see the Privacy Foundation's
Bugnosis webbug detector ( http://www.bugnosis.org/ - Windows MSIE only).
When webbugs are loaded into popup pages, the solution is to close the popups
(usually a small page with an ad, though some of them are 'micropages'
that you can barely see. A few may even use javascript tricks to keep
you from closing them. If this happens, close all other browser windows,
then you should be able to close the bug window). Another tip for defeating
webbugs is to reject any cookies from Doubleclick, AdCast, LinkExchange and other
'ad exchange networks' (cookie sharing rings), and any other cookies that
are not from the site you are currently visiting (most third-party cookies
are basically webbugs). Lastly on this topic, be aware that HTML-capable
e-mail programs and Usenet newsreaders make webbugs work in your e-mail
and newsgroups. If your mailer or newsreader has an option to turn off
cookie support, you should certainly do so. There is hardly any imaginable
legitimate use for a cookie in an email or a newsgroup posting.
9) Be conscious of home computer security.
On the other side of the coin, your own computer may be a trouble
spot for Internet security.
If you have a DSL line, broadband cable modem or other connection
to the Internet that is up and running 24 hours (including T1 at the office without a firewall
or NAT),
unlike a modem-and-phone-line connection, be sure to turn your computer off
when you are not using it. Most home PCs have pitifully poor security
compared to the Unix workstations that power most commercial Web
sites. System crackers search for vulnerable, unattended DSL-connected
home computers, and can invade them with surprising ease, rifiling
through files looking for credit card numbers or other sensitive data,
or even 'taking over' the computer and quietly using it for their own
purposes, such as lauching attacks on other computers elsewhere -
attacks you could initially be blamed for. Firewall hardware and software is
another option that can protect you from these kinds of attacks (available
at any computer store; freeware and shareware implementations may be
available at sites like http://www.shareware.com
or http://www.download.com.
10) Examine privacy policies and seals.
When you are considering whether or not to do business with a Web
site, there are other factors than a secure connection you have to consider that are equally
important to Web security. Does the site provide offline contact
information, including a postal address? Does the site have a
prominently-posted privacy policy? If so, what does it say? (Just
because they call it a 'privacy policy' doesn't mean it will protect
you - read it for yourself. Many are little more than disclaimers
saying that you have no privacy! So read them carefully.) If the
policy sounds OK to you, do you have a reason to believe it? Have you
ever heard of this company? What is their reputation? And are they
backing up their privacy statement with a seal program such as TRUSTe
http://www.truste.org/ or
BBBonline http://www.bbbonline.org/? (While imperfect, such
programs hold Web sites to at least some minimal baseline standards, and may revoke, with much fanfare, the
approval-seal licenses of bad-acting companies that do not
keep their word.) If you see a seal, is it real? Check with the
seal-issuing site to make sure the seal isn't a fake. And examine
terms carefully, especially if you are subscribing to a service rather
than buying a product. Look out for auto-rebilling scams and hidden
fees.
11) Remember that YOU decide what information about yourself to
reveal, when, why, and to whom.
Don't give out personally-identifiable information too easily. Just as
you might think twice about giving some clerk at the mall your home
address and phone number, keep in mind that simply because a site asks
for or demands personal information from you does not mean you have to
give it. You do have to give accurate billing information if you are
buying something, of course, but if you are registering with a free
site that is a little too nosy for you, there is no law (in most places) against
providing them with pseudonymous information. (However, it would
probably be polite to use obviously fake addresses, such as '123 No
Such Street, Nowhere, DC 01010'. If they are generating mailings based
on this information - presumably in accordance with the terms of their
privacy policy - they can probably weed such addresses out and not
waste the postage on them. Definitely do NOT use someone else's real
address!)
However, if you are required to agree to
terms of service before using the free service, be sure those terms
do not include a requirement that you provide correct information,
unless the penalty is simply not being allowed to use the service
any more, and you're willing to pay that price if they figure out
you are not providing them with your actual personally-identifiable
information.
12) Use encryption!
Last but certainly not least, there are other privacy threats
besides abusive marketers, nosy bosses, spammers and scammers. Some
of the threats include industrial espionage, government surveillance,
identity theft, disgruntled former associates, and system crackers.
Relatively easy-to-use e-mail and file encryption software is
available for free, such as Pretty Good Privacy (PGP, available at: http://www.pgpi.org/), which runs on
almost all computers and even integrates seamlessly with most major
e-mail software. Good encryption uses very robust secret codes, that
are difficult if not impossible to crack, to protect your data. You
can also use specialized services (some free, some pay)
that go beyond infomediary services, including running all connections
through a securely encrypted 'tunnel', anonymous dialup, even anonymous
Web publishing. Another type of product is SSH tunnelling (port forwarding) packages, such as FSecure SSH ( http://www.fsecure.com/products/ssh/ ),
and SecureCRT ( http://www.vandyke.com/products/securecrt/ ).
Hopefully some day soon, good encryption and computer security will simply
be included in all ISP services and operating systems, but for now you have to actively
seek out good service providers and add-on products.
For more information on protecting your online privacy:
- EFF Privacy Archive - http://www.eff.org/Privacy/
- 'Protecting Yourself Online' Book -
- TRUSTe's 'Protecting Your Privacy Online' FAQ - http://truste.org/consumers/users_faqs.html
- Privacy Rights Clearinghouse - http://www.privacyrights.org/
- Privacy International - http://www.privacyinternational.org/
Over the last few decades, the world has changed tremendously in many regards, especially when it comes to IT. The number of people we are able to communicate with on a daily basis has grown enormously, just like the amount of information we have access to. However, the same is true for the amount of information big companies collect about us. Terms such as big data are used all the more frequently as time goes on. But what does this mean, exactly? What is big data? Is it dangerous? How does it affect our privacy, if at all? Those are some of the questions we'll cover in this article.
What is big data?
The term 'big data' describes the enormous quantities of (personal) data which are continuously being gathered by different actors. An example would be all of the information Google gathers about its users' search queries. The phenomenon of big data is a relatively recent development that started because (large) companies and organisations, such as Facebook, Google and most governments, started to gather ever more data about its users, customers and citizens than before. New technologies, a digitized world and the internet have aided this development immensely.
Collections of big data are often so vast that it's impossible to analyze them using traditional data analysis. However, if one analyses big data the right way, interesting patterns and conclusions can be induced. For instance, big data is often used for large scale market research: which products are most likely to be purchased? What kind of advertising is most effective when you want to reach and persuade customers?
In order for a dataset to be considered big data, it should usually meet the following three criteria, also known as the 3 v's:
- Volume: Big data is anything but a small sample. It involves vast collections of data, resulting from long, continuous observation.
- Velocity: This has to do with the impressive speeds at which big data is collected. Moreover, big data is often accessible in real time (as it is being gathered).
- Variety: Big datasets often contain many different types of information. Data within big data-sets could even be combined to fill in any gaps and make the dataset even more complete.
Aside from these 3 v's, big data has some other characteristics. Mind dead 1 0. For example, big data is great for machine learning. This means it can be effectively used to teach computers and machines certain tasks. Moreover, as we've already briefly touched upon, big data can be used to detect patterns. This mostly happens in a very effective way, by means of computers working on the data. Finally, big data is the reflection of users' digital fingerprints. This means it's a by-product of people's digital and online activities and can be used to build individual personal profiles.
Different kinds of big data
There are different ways to classify big data. Allavsoft spotify. The first way, which is used most frequently, differentiates big data based on the kind of data which is being collected. The three possible categories used for this type of classification are: structured big data, unstructured big data and semi structured big data.
- Structured: When big data is structured, it can be saved and presented in an organised and logical way, making the data more accessible and easier to comprehend. An example would be a list of customer addresses created by a company. In this list, one would likely find customers' names, addresses and maybe other details such as phone numbers, all structured clearly in, for example, a chart or table.
- Unstructured: Unstructured big data is not organised at all. It lacks a logical presentation which would make sense to the average human being. Unstructured big data doesn't have the structure of, for instance, a table that denotes a certain coherence between the different elements of the data set. Hence this type of data is quite difficult to navigate and comprehend. Many datasets initially start out as unstructured big data.
- Semi-structured: Semi-structured big data, as you might have guessed, has characteristics of both structured and unstructured big data. The nature and representation of this type of data aren't completely arbitrary. Yet it isn't structured and organised enough to be used for a meaningful analysis, either. An example would be a web page which contains specific meta data tags (extra information which isn't directly visible in the text), for instance because it contains certain keywords. These tags effectively show specific bits of information, such as the author of a page or the moment it was placed online. The text itself is essentially unstructured, yet the keywords and other meta data it contains help to make it a somewhat suitable basis for analysis.
Classification based on the source of big data
Another common way to distinguish between different kinds of big data is by looking at the source of the data. Who or what has generated the information? Like the previous division, this classification method also consists of 3 different categories.
- People: This category concerns big data generated by people. Examples would be books, pictures, videos as well as information and (personal) data on websites and social media, such as Facebook, Twitter, Instagram, and so on.
- Process registration: This category includes the more traditional kind of big data, which is gathered and analysed by (big) companies to improve certain processes in a business.
- Machines: This type of big data results from the ever growing number of sensors that are placed in machines. An example would be the heat sensor that is often built into computer processors. The data generated by machines can often be very complex, but at least this type of big data is generally well-structured and complete.
What can big data be used for?
Everything discussed so far might still sound somewhat abstract. Let's make things a little bit more concrete and discuss some real-life applications of big data. After all, there are many, many ways in which companies and organisations use big data. One of the first things that comes to mind is the enormous amounts of data companies gather about us. Facebook collects data on all of its users and analyses this to decide what to show you on your timeline. Of course, this is done to cater to your personal wishes and interests. Facebook hopes this will get you to stay on their website for longer periods of time. In turn, Amazon gathers information about its clients and the products they buy. That way, Amazon can recommend products they think you'll be interested in and increase their earnings this way.
However, big data is also used in ways completely different from the commercial strategies described above. For instance, public transport companies can gather data about how busy certain routes are. Afterwards, they could analyse this data to decide, for example, which routes require additional buses or trains. Another well-known case of effective use of big data concerns international delivery giant UPS. UPS uses special software which was developed after big data analysis. This software helps UPS drivers avoid left-hand turns, which are costlier, more wasteful and more dangerous than right turns. Supposedly, this system has already saved UPS millions of gallons in fuel, all thanks to big data.
Another interesting example of big data gathering are DNA tests and websites such as MyHeritage DNA. This website claims it can help you 'uncover your ethnic origins and find new relatives' with a simple DNA test. Needless to say, this process involves a lot of data gathering and cross-referencing, making it another major player in big data gathering and usage. 'Traditional', physical DNA tests also involve a huge amount of big data, since companies who conduct these tests will gain extremely large data sets about many, many people. Of course, it's important to be aware of the possible risks that come with these big data gathering processes. These risks will be highlighted in the next part of this article.
Is big data dangerous?
As shown above, big data can be incredibly useful in many cases. It provides us with tons of information we can use to streamline processes and make companies more efficient and profitable. However, this doesn't mean gathering and using big data is completely risk-free. There are five important risks that come with big data. We'll be discussing all five here.
Hackers and thieves
With everything we do online, there's an inherent risk that our personal data and information on our internet activities could be stolen. Every internet user has to be aware of this. The number of data leaks and thefts has increased drastically over the past few years. There are often stories in the news about criminals selling data sets containing passwords and other information on places such as the dark web. Often, these data sets are stolen from official websites, companies and organisations. The bigger these data sets are, the more interesting it becomes for thieves to try to obtain them. If they get their hands on these data sets, they could cause a lot of problems. Needless to say, this could also greatly compromise your privacy.
Privacy
The practice of gathering personal data is becoming more and more widespread. However, the current privacy regulations can't keep up with the rapid developments in technology that makes this practice possible. This leaves space for grey areas and uncertainties that can't be solved by looking at the law. Important privacy concerns that arise include: What kind of data is allowed to be collected? About whom? Who should have access to this data?
When collecting large amounts of data, chances that sensitive personal information is included in those datasets are high. This is problematic, even when hackers and thieves aren't at play. After all, privacy-sensitive data could be abused by anyone with ill intentions. This includes (malicious) companies and organisations.
Poor data-analysis
Many companies and organisations collect big data, because they can use it for interesting analyses. This might give them important new insights into whatever they're researching (like, for example, consumer habits). In turn, these insights and conclusions could translate to changes within the company that result in higher margins and more profit. However, just like with any other normal dataset, an incorrect analysis of big data can have serious consequences. After all, an improper analysis can easily lead to wrong conclusions. These can in turn translate to ineffective or even counterproductive measures being taken.
Gathering the 'wrong' data
Big data is becoming increasingly popular and organisations are more and more willing to collect all sorts of data. This means gigantic amounts of data are being collected without there being a clear reason for analysing them. In other words, it creates a huge database of raw information that has been gathered just in case. Companies are likely thinking it's easy enough to gather all that data, so they might as well do it. Needless to say, this isn't good for anyone's privacy. It could even lead to irrelevant or 'wrong' data being gathered and analysed. If the conclusions drawn from this analysis are used in management, it could lead to the same ineffective measures mentioned in the previous paragraph.
Collecting and saving big data with ill intentions
The collection of big data is used more and more often by companies, organisations and governments so they can make accurate individual profiles on people. Users or citizens are hardly ever notified about which of their personal data is being registered, let alone why and how. Needless to say, this has serious implications for their online privacy. Everything they do online, can be saved and viewed later. Moreover, big data collectors could easily influence and manipulate people's decision making by analysing and using the collected data.
Big data and privacy
As you'll probably understand by now, big data comes with a lot of disadvantages and risks. Nevertheless, many companies and organisations still collect data on a huge scale, mostly because of how it can help them grow and advance. Collecting big data is easier than ever before. This has huge consequences for our privacy. We've already briefly discussed the possible privacy dangers of malicious parties collecting bad data. Since our privacy is so closely tied to the mass collection of personal data, we want to use this section to discuss the different privacy concerns that come with big data.
Large scale data collection
Lots of companies, including Google, Facebook and Twitter, are heavily dependent on advertisements to sustain themselves and make a profit. To make these ads as effective as possible, these companies make detailed profiles on their users, especially taking their likes and interests into account. This is a form of big data. Likewise, governments and secret services are dependent on big data as well. They use this vast amount of information to track and investigate people they deem suspicious. Of course, this also means there's a lot of big data for cyber criminals to get their hands on and maybe even manipulate and abuse. This can create all sorts of privacy and identity-related problems. One that comes to mind, is identity theft.
Still, the possibilities that come with the collection in databases are much broader than this. These days, technology has become so advanced and 'smart' that it can combine data sets. This can be done in such a clever and crafty way, that large corporations and organizations likely know more about you than you do! Who you are, where you live, what your hobbies are, who your friends are: none of this information will be private any longer. Not a very comforting thought, you might think. Fortunately, there are some ways to protect yourself from the large scale privacy infringement big data can cause.
Laws on privacy
Privacy laws and regulations can protect us against privacy infringement, but only up to a certain extent. To make matters more complicated, privacy laws often differ greatly between different countries and regions. For instance, in Europe a relatively strict consumer privacy law called the General Data Protection Regulation (GDPR) is in force. This law applies to all EU member states, although the details might differ per country. Many international companies have decided to abide all of their business to the GDPR. This is why Google, for example, now allows users to request a deletion of personal information. However, privacy laws in the United States differ from state to state and don't protect consumers as well as the EU. Unfortunately, this is even true for the toughest privacy law in the US, the California Consumer Privacy Act.
In short, there's no such thing as a strong 'global' privacy law that applies to all big data collectors and protects all users. This means our privacy is not just harmed by big data-collectors in illegal, but even in perfectly legal ways, as paradoxical as this may sound. Fortunately, large-scale privacy infringements exposed by whistle blowers like Edward Snowden and Chelsea Manning have greatly increased awareness for the risks of big data. Of course, this is only a first step in improving current privacy laws.
Many internet users aren't willing to await an improvement in privacy laws – and rightfully so. Rather, they want to take action themselves by doing whatever they can to protect their privacy. Do you want to avoid becoming part of countless big data-sets as well? There are several tips and tricks to help you on your way.
Cookie 4 5 4 – Protect Your Online Privacy Policy
How to keep your data from being saved in big data-sets
Cookie 4 5 4 – Protect Your Online Privacy Rule
Big datasets seriously affect your privacy and security. These datasets might contain all sorts of (personal) information, which could be abused by big companies or even cyber criminals. That's why you should always make sure to leave as little of an online trace as possible. The following tips can help you accomplish this:
Cookie 4 5 4 – Protect Your Online Privacy Statement
- Try to minimize the use of your personal information when creating passwords or in general on the web. For instance: avoid using your name, address, phone number, date of birth, and so on.
- Always remember the following: everything you publish on the internet, will be on there forever. This might not always be completely true, but this level of caution does help safeguard your privacy. You'll automatically handle your private data with more care once you're aware of this fact.
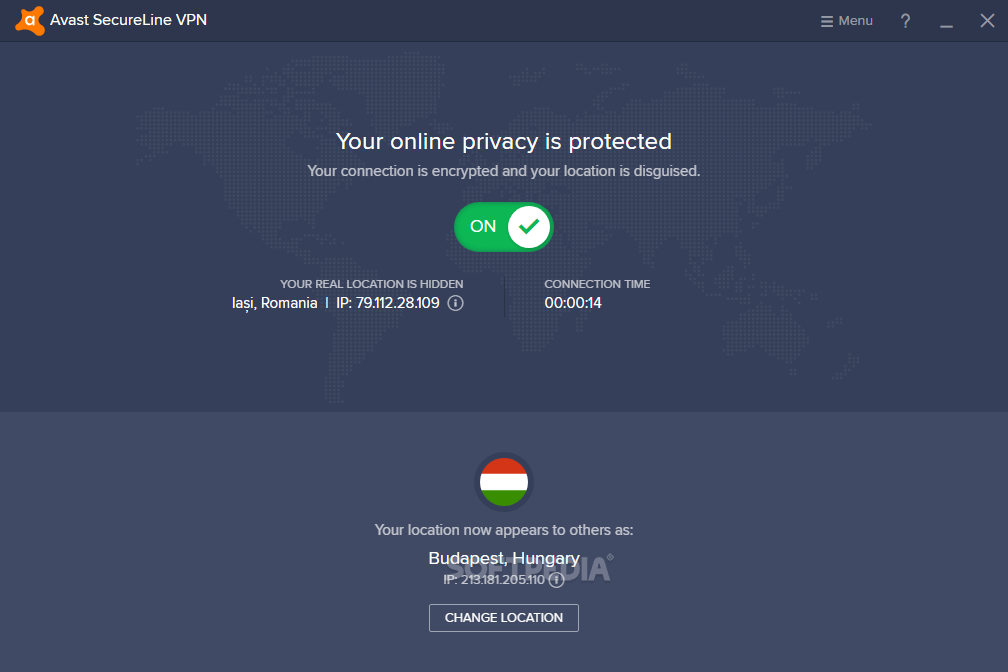
- Make sure your internet connection is secure and anonymized, for example by using the Tor-browser or a VPN for example.
- Use one or several ad-blockers in your browser.
- Use on or more browser plug-ins which block trackers and cookies.
- Regularly clear your cache and delete your browsing history and cookies.
- Log out of websites when you're not actively using them.
Taking these steps is a good start when it comes to safeguarding your online privacy and security. Keep in mind, however, that big data is collected in many different ways – not just online. In short, wherever you are and whatever you're doing, you should always be vigilant and try to protect your (personal) data from big data-collectors.

